thick application testing|thick client software : inc Application Security Testing | Solutions to address security risks at all stages of the application life cycle. DevSecOps | Solutions to help shift security left without slowing down your development teams. Software Supply Chain Security | Solutions to identify and manage software supply chain risks end-to-end. 24 de set. de 2023 · Você pode gostar. 6.8K curtidas,131 comentários.Vídeo do TikTok de Fan Clube (@catarinapaolinofc): "Catarina Paolino | Fala Sobre Seu Only F4ns #catarinapaolino .
{plog:ftitle_list}
WEBJogos de Ovelhas no Jogos 360 online, 100% grátis. Os melhores e mais novos Jogos de Ovelhas, animais, habilidade, empilhar, obstáculos, agilidade, jogo, shaun the sheep sheep stack, shaun the sheep, shaun o carneiro, shaun para jogar grátis no Jogos 360
How to test thick client applications? 👨💻. Thick Client Pentest is complicated as compared to /API Pentest in my opinion. In Thick Client, there are two types (i) Proxy-based Thick clients. (ii) Non-Proxy based thick .What is Thick Client Application Security? Thick Client Application Overview. Thick client are type of applications which run on user’s host machine/system and communicate with backend server or database server. Few of the examples are listed below: Microsoft Teams; Outlook; Skype; With respect to architecture, they are classified as two tier .
Application Security Testing | Solutions to address security risks at all stages of the application life cycle. DevSecOps | Solutions to help shift security left without slowing down your development teams. Software Supply Chain Security | Solutions to identify and manage software supply chain risks end-to-end.To learn the Thick Client Application Penetration Testing concepts by practicing, it is important to have a lab where we can practice everything in a legal environment. Vulnerable Application Design: DVTA application is developed using C#.NET in Microsoft Visual Studio. This client communicates with SQL Server and an FTP Server that are running .Attack surface visibility Improve security posture, prioritize manual testing, free up time. CI-driven scanning More proactive security - find and fix vulnerabilities earlier. Application security testing See how our software enables the world to secure the web. DevSecOps Catch critical bugs; ship more secure software, more quickly. Penetration testing Accelerate penetration testing - find .Thick client applications are more complicated and customized as compared to web or mobile applications.This makes the pen testing approach for thick client applications very different. A very specific approach to testing these applications is followed after understanding the application in terms of technologies used, functionality, behavior .
thin client vs thick client
thick client software
Test for Client-side protection bypass using reverse engineering; Test For Function Exported. Try to find the exported functions; Try to use the exported functions without authentication; Test For Public Methods. Make a wrapper to gain access to public methods without authentication; Test For Decompile And Application Rebuild
When it comes to thick client penetration testing, there are several tools that are commonly used by security professionals. One such tool is Burp Suite, which is a powerful platform for performing security testing of web applications.It provides functionalities like intercepting and modifying network traffic, performing code analysis, and executing exploits. Thick client application security testing is a process that evaluates the security of desktop applications by identifying vulnerabilities, testing authentication mechanisms, assessing data encryption, addressing security misconfigurations, and investigating network communication to ensure the robustness and integrity of thick client software.
thick client security testing
Welcome to the Thick Client Penetration Testing Repository! This repository aims to familiarize you with Thick Client Application security concepts, providing a comprehensive guide and practical methodology for thick client Pentesting. Whether you're a . Thick client penetration testing is a security assessment process that focuses on identifying and mitigating vulnerabilities in applications that run on client devices, such as desktops or mobile. Test Defenses Against Application Misuse 10.8. Test Upload of Unexpected File Types 10.9. Test Upload of Malicious Files 10.10. Test Payment functionality . They are quite different from web services in the sense that thick applications, most of the tasks are performed at the client end, so these apps heavily depend on client's system . Thick Client Application Penetration Test: What It Is and How to Do It. Thick client penetration testing is a security assessment process that focuses on identifying and mitigating vulnerabilities .
thick client security
Holistic Security Approach: While web applications are commonly tested, thick client penetration testing ensures a comprehensive security approach, addressing vulnerabilities unique to locally .Testing thick client applications for security vulnerabilities requires expert manual penetration testing skills and a thoughtful, methodical approach. NetSPI’s thick client app penetration testing uses multi-vector cybersecurity testing to identify design and configuration weaknesses.Learn practical thick client application penetration testing techniques. How to reverse engineer .NET binaries. Students will learn how to patch .NET binaries. How to identify and exploit common security issues in 2-tier applications. Learn multiple ways to intercept TCP traffic coming from thick client apps Thick Client Application Testing Methodology. Discovery. Compared to Thin Client Applications, Thick Client Applications are custom-built and hence are relatively complicated. So it becomes prudent to gather all .
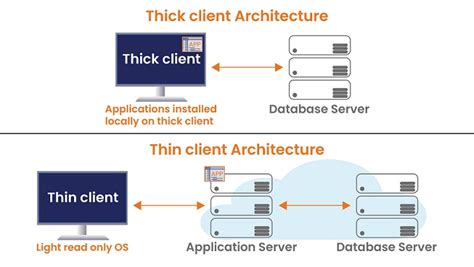
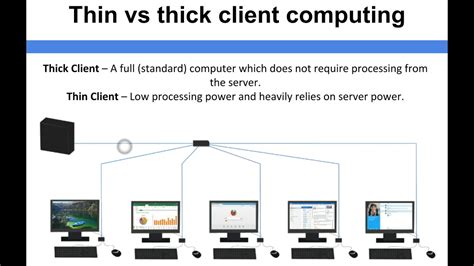
If a thick client is built on a three-tier architecture, the network portion of the test will essentially be the same as testing a web application. First order of business is proxying the traffic. In the proxy tab of Burp, set up a .This course introduces students to the penetration testing concepts associated with Thick Client Applications. This is an entry level to intermediate level course and we encourage you to take this course if you are interested to learn Thick Client Application Security. What is Thick Clients? A thick client is a system that can be connected to the server even without the network. Thick clients are also referred to as heavy or fat clients. Thick clients are not dependent on the server’s applications. They have their own operating system and software applications. They have high flexibility and high server .
Testing thick client applications, for example, requires patience and a systematic approach, and simple automated assessment scanning does not suffice. A custom set-up is often necessary, as well as specialized tools. The architecture of thick clients Two-Tier architecture.Thick client application testing is generally more complicated and customized, involves both local and server-side processing, and often uses proprietary protocols for communication aimed at detecting and identifying loopholes and vulnerabilities before they are exploited for malicious gain. Simple automated scanning is not sufficient and .
thick client pentest
Thick Client Penetration Testing (a.k.a. Thick Client Pentest, Thick Client VAPT, Thick Client Pen Testing) identifies exploitable vulnerabilities on both the local and server-side. The attack surface is larger and requires a different approach from web application penetration testing. Such process often requires specialized tools and custom .
single end yarn strength tester store
To test a thick client application the most important task is intercepting the requests fired by the application. On the basis of this benchmark, it can be classified as follows: 1. When testing any application, it’s important to have a good understanding of what’s going on beneath the surface. Consider the largest desktop application you’ve ever seen – that’s like half of the thick client applications I test. They’re monuments to teamwork and the human spirit. I once had six hours of demos for a test, and the .
Introduction to Thick Applications. 2. Why Pentesting Thick Applications is Important. 3. Common Security Risks and Vulnerabilities. 4. Tools and Techniques for Pentesting. 5. Vulnerable Labs of .
single yarn strength tester diagram store
Testing of a thick client application. There are three stages of thick client application testing. Dynamic Testing; System Testing; Static Testing; Dynamic testing. In this phase of testing, we analyze the data transfer from the client application to the application server. Test cases in this phase are as follows. Input ValidationThe TASVS Project fills the gap between the OWASP Application Security Verification Standard (ASVS) for web applications and the Mobile Application Security Verification Standard (MASVS). While the MASVS can be applied to thick client testing, it is not an ideal fit. The TASVS Project seeks to create a more suitable standard for these scenarios.
single yarn strength tester manufacturers store
single yarn strength tester pdf store
webDMT Extraction & ROA Harm Reduction | Learn, Share & Discuss. A harm reduction focused subreddit for discussing the processes involved in the extraction of DMT along with routes of administration (ROA), as well as a central repository for extraction guides and ingestion methods. Remember to flair your posts and choose an appropriate user flair.
thick application testing|thick client software